Contributed by sean on from the squashing-the-low-hanging-fruit dept.
Using OpenBSD and spamd for spam filtering and grey-listing is very old news but there are a few situations where it becomes politically and technically challenging to run in production. Here was a simple yet (and in no way the best method) of using PF and some friends on the internet to help 'slow the flow' of offal from the Internet into your mail server.
The spamd application is fantastic. It does a great job at giving back to the spammers that annoy us. It does have some flaws that in certain environments leave us to find other solutions.
For instance some web-mail services (like Gmail) rarely re-deliver on delay from the same server making it exceedingly difficult to put their network into a white-list and to make matters worse there are so many outgoing MTA IPs that seem to change faster than you can collect them. The second nail in my 'default spamd' coffin is dealing with clients that use broken or 'I clicked till it worked' installations of Exchange services. I don't know how many times some random client would get caught in the tar pit and lead to many last minute and out of band support calls (usually while I was indisposed and away from any form of SSH capable device). One client in particular fiddled with their stuff so often I just white-listed the entire net block the whois advertised that just to make them shut up.
Needless to say, spam piled up at a ridiculous rate. I had to leave my mail client open 24x7 to filter the flood in my own mail account. At one point we were receiving 100,000+ pieces of spam per day across our low triple digit user base. The mail server couldn't hack it. Leaving your machine off for the weekend made your account useless on Monday morning and deus-ex-machina help you if you went on vacation.
Thunderbird's spam filter is crap but helped some users. Another help for the more 'popular' users was Mail Washer and that helped but eventually we just gave up trying and secretly turned spamd back on and waited for the complains before we turned it off again.
Spamassassin wasn't an option as the mail server was already over-subscribed and heavily internal mailing list use (mailman) and aggressive IMAP clients would render the machine almost unusable. The record load was 140 lasting for a good hour or so. Of course like most fiscally aggressive companies, budget for a more reasonable mail infrastructure to scale with the amount of users we now have will only become available when the machine up and dies good and proper. The urge to do what we can with what we have is frustrating but I love a good challenge.
We even flirted with the idea of using a different grey-lister solution that was less elegant than spamd but would allow for domain name based white listing and was essentially a front end filter to sendmail. That's not even addressing the rather high frequency of false positives from bulk-email services (Gmail, Yahoo Mail, Hotmail, etc.). I really didn't want to go down this road since I'm a fan of sticking with 'base' as aggressively as possible.
After a particularly frustrating Monday morning, and fielding a question about available IP based spam filtering for 'the Linux' a solution became all to clear. Not everything has to go through spamd (or at all) and we don't need grey-listing. All we really need to do is collect various 'black and gray lists' from others and tar pit them (with periodic flushes). The other advantage here is that it can be extended to work on systems that don't have spamd or PF (or in conjunction with spamd... 'for extra win').
So I went searching around for a bunch of black and grey-lists and collected a nice little list, and then wrote a stupid script to pull them and pop them into a black-list pf table which just drops all traffic from those hosts (or alternatively redirecting them to the spamd tar pit). The results were mind blowing. No other form of spam filtering is being done, and my personal spam to ham ratio went from 1000:1 to 1:1000. I left this solution in place for a good while (about a year and a bit) without complaints (and surprisingly few user noticed given the volume of complains) and I no longer field those horrendous support calls nor random meetings with client IT personnel explaining why they can't send us mail.
The solution here is pretty simple. Use a normal spamd config and instead of redirecting everything save spamd-white entries just send anything in the black-list to spamd (or just drop it entirely) and if it gets out of the tar pit... that's tolerable (loggable, and easy to monitor). I call it 'social passive aggressive filtering.'
Even if your filtering systems are not OpenBSD based the method stays the same.- Gather your blacklists from around the net.
- Translate them into a format your filter/firewall can understand.
- Load them in.
- Every regular period flush the blacklist and go back to one.
/root/bin/update_traplist.shtable <whitelist> persist file "/etc/spamd/whitelist.txt" table <blacklist> persist file "/etc/spamd/traplist.txt" set limit table-entries 200000 rdr pass from <blacklist> to port smtp -> localhost port spamd #If you can't get away with tar-pitting the jerks just dump'em! #pass quick from <whitelist> to port smtp #block drop from <blacklist> to port smtp
#!/bin/sh
# Don't care about dup's as the pf table add will select uniques.
$LIST=/tmp/spamd-black.txt.tmp
lynx --source http://www.openbsd.org/spamd/traplist.gz >> $LIST
lynx --source http://www.openbsd.org/spamd/spews_list_level1.txt.gz >> $LIST
lynx --source http://www.openbsd.org/spamd/spews_list_level2.txt.gz >> $LIST
lynx --source http://www.openbsd.org/spamd/SBL.cidr.gz >> $LIST
lynx --source http://www.openbsd.org/spamd/chinacidr.txt.gz | awk '{print $1}' >> $LIST
lynx --source http://www.openbsd.org/spamd/koreacidr.txt.gz | awk '{print $1}'| sed ';' ' ' >> $LIST
# Column 2 is all we care about here.
lynx --source http://www.ix.de/nixspam/nixspam.blackmatches | awk '{print $2}' >> $LIST
# Sometimes stray semi-colons show up and bung up the works.
lynx --source http://www.bsdly.net/~peter/bsdly.net.traplist | sed ';' ' ' >> $LIST
lynx --source http://www.spamhaus.org/DROP/drop.lasso | sed ';' ' ' | awk '{print $1}' >>$LIST
mv $LIST /etc/spamd/traplist.txt
# Here's the magic!
pfctl -t blacklist -T replace -f /etc/spamd/traplist.txt 2>/dev/null
The peroidic part is easy... just run this script in root's crontab!
0 */6 * * * /root/bin/update_traplist.sh 2>/dev/null
For the purposes of the article I tracked the number of blocked IP's on my busiest two mail servers and the following pretty pictures illustrate the variability of the spam hosts in the above list.
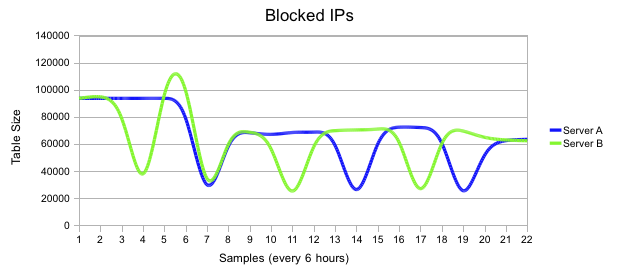
This by no way is a good, clever or novel solution, it was just one that made a HUGE impact on the users I service and an even bigger impact on the abuse of our overloaded mail server. This is also a pretty old solution, but on the odd chance someone hasn't come to this conclusion here is something else to try.
I would love to say 'well we don't want to work with people that can't fix their own mail server.' but that's not good for business. Note the emphasis here is on blocking the low hanging fruit as seen by other less constrained networks. Of course it would be prudent to note that the lists you chose should come from systems you trust and using white-lists to ensure some VIPs and your own networks are not black-holing is probably a good idea too.
Part 2... I'm an idiot.
After all this work and effort a casual look at the man page shows that spamd in blacklisting mode does exactly all of this and better. Insert face-palm here. The solution was right in front of my face the whole time and ended up over-engineering my solution.
The 'right way' to solve this problem is very similar:
/etc/pf.conf/etc/rc.conf.localtable <spamd-white> persist file "/etc/spamd/whitelist.txt" table <spamd> persist;" set limit table-entries 200000 rdr pass from <spamd> to port smtp -> localhost port spamd #If you can't get away with tar-pitting the jerks just dump'em! #pass quick from <spamd-white> to port smtp #block drop from <spamd> to port smtp
/etc/mail/spamd.conf# Run spamd in blacklisting mode only. spamd_flags="-b"
all:\
:spews1:spews2:bsdly:china:korea:spamhausDROP:nixspam:
nixspam:\
:black:\
:msg="Your address %A is in the nixspam list\n\
See http://www.heise.de/ix/nixspam/dnsbl_en/ for details":\
:method=http:\
:file=www.openbsd.org/spamd/nixspam.gz:
bsdly:\
:black:\
:msg="SPAM. Your address %A is in the BSDLY traplist\n":\
:method=http:\
:file=http://www.bsdly.net/~peter/bsdly.net.traplist:
spamhausDROP:\
:black:\
:msg="SPAM. Your address %A is in the Spamhaus DROP List\n\
See http://www.spamhaus.org/sbl and\
http://www.abuse.net/sbl.phtml?IP=%A for more details":\
:method=http:\
:file=www.spamhaus.org/DROP/drop.lasso:
# Mirrored from http://www.spews.org/spews_list_level1.txt
spews1:\
:black:\
:msg="SPAM. Your address %A is in the spews level 1 database\n\
See http://www.spews.org/ask.cgi?x=%A for more details":\
:method=http:\
:file=www.openbsd.org/spamd/spews_list_level1.txt.gz:
# Mirrored from http://www.spews.org/spews_list_level2.txt
spews2:\
:black:\
:msg="SPAM. Your address %A is in the spews level 2 database\n\
See http://www.spews.org/ask.cgi?x=%A for more details":\
:method=http:\
:file=www.openbsd.org/spamd/spews_list_level2.txt.gz:
# Mirrored from http://www.okean.com/chinacidr.txt
china:\
:black:\
:msg="SPAM. Your address %A appears to be from China\n\
See http://www.okean.com/asianspamblocks.html for more details":\
:method=http:\
:file=www.openbsd.org/spamd/chinacidr.txt.gz:
# Mirrored from http://www.okean.com/koreacidr.txt
korea:\
:black:\
:msg="SPAM. Your address %A appears to be from Korea\n\
See http://www.okean.com/asianspamblocks.html for more details":\
:method=http:\
:file=www.openbsd.org/spamd/koreacidr.txt.gz:
root's crontab:
0 * * * * /usr/libexec/spamd-setupThis is far better for a few reasons.
- The periodic updates are done by spamd-setup which is written far better than my script could ever be and is easily appended to without worrying about fat-fingering something (spamd-setup will fail if the configuration is messed up).
- spamd and spamd-setup are in base and are supported.
- Aside from spamd's rather weird configuration file (well weird to me) it is far less error prone.
(Comments are closed)

By Andreas Vögele (85.216.54.124) on
Comments
By Anonymous Coward (217.197.149.135) on
How do you download the list? By rsync?
Comments
By Anonymous Coward (85.216.54.124) on
>
> How do you download the list? By rsync?
See http://www.dnswl.org/tech#rsync for details.
In the past month 36 percent of the spam messages that got through our spam filter originated from Hotmail, Yahoo or Gmail. Greylisting doesn't help against these spam messages and normally you don't want to blacklist web mail providers.
Comments
By Anonymous Coward (217.197.149.135) on
>
>
> How do you download the list? By rsync?
>
> See http://www.dnswl.org/tech#rsync for details.
>
> In the past month 36 percent of the spam messages that got through our spam filter originated from Hotmail, Yahoo or Gmail. Greylisting doesn't help against these spam messages and normally you don't want to blacklist web mail providers.
Thanks. But do you know about any solution how could I use this list or perhaps some other whitelist list with base tools in OpenBSD? To be honest I don't like an idea to install rsync on production server just to get the list.
Comments
By Matthew Dempsky (67.215.69.60) on
Why? rsync is a pretty simple command. It's basically a smarter version of scp.
By Kb (82.120.241.138) on
I think you miss "file=" line from the "spamhaus" section in your spamd.conf example.
As far I recall, spews, sbl and spfilter.openbrl.org datas are unusable since 2006 for some of them.
spews_list_level(1|2).txt mirrors from OpenBSD are juste empty.
Cya
Comments
By Sean Cody (sean) on I don't work here.
>
> I think you miss "file=" line from the "spamhaus" section in your spamd.conf example.
>
> As far I recall, spews, sbl and spfilter.openbrl.org datas are unusable since 2006 for some of them.
> spews_list_level(1|2).txt mirrors from OpenBSD are juste empty.
>
> Cya
>
>
Fat fingered a few things obviously.
Removed spamhaus from the config above. Thanks.
I pulled most of this from a stock spamd.conf from a machine running a few versions behind.
What I would really like to see is a clearing house for greytrap lists similar to Beck's and BSDLY's lists but from a bunch of mail servers all over. That would be fantastic (the slacker in me just kicked in).
Comments
By Peter N. M. Hansteen (pitrh) peter@bsdly.net on http://bsdly.blogspot.com/
if you run your own greytrapping, it takes literally about five lines of shell script to generate a list of trapped addresses that can be fed to other spamds.
combining data from several sources should be equally easy and in fact i would love to contribute to such an effort.
- Peter
By Kurt (68.151.57.38) kurt@seifried.org on
By Daniel Gracia (paladdin) guardame_el_secreto@yahoo.es on http://www.alpuntodesal.com
By the way, just one detail to comment: In this days I've seen several scripts making use of wget, lynx and others to recover files from web servers, when it should be noted that ftp itself has support to recover files from http protocol as easy as 'ftp http://myserver.com/myfile.tgz' :)
By sthen (85.158.44.149) on
Comments
By Anthony (2001:470:81c2:200:207:e9ff:fe39:24e8) on
That's exactly what I do. Even the aggressive ones with big netblocks aren't that big a deal when all they get is greylisted.
pfctl -t rbl -T replace -f /tmp/concated_lists
This removes IPs that aren't in the file anymore, and adds new ones that are. All it needs is a newline delimited file. I recommend the AMD64 port, i386 is limited to 768 mb of kernel memory and AMD64 is 4 gigs. That'll get you 15+ million table entries, which goes a long way when some of them are big prefixes from aggressive lists.
By Nudzo (2002:59ad:5eeb:1:214:4fff:fe0f:e7d4) ivan.nudzik@gmail.com on
1. it took in common 1-2 day to go through gray list when sender has more mail server... for example gmail. But when it is in white list, everything works fine. Sometimes it is hard to explain it to BFU, cause they about mail the same way as instant messaging. ;-)
2. I've put spamd only to filter mail going from internet. Users has other IP/DNS with the real mailserver, which only accepts mail after authorization, so users can send mail out instantly. OpenBSD queues mails from internet in its sendmail and forward it then to real mailserver with accounts.
3. When other servers going down overloaded by spamassassin, OpenBSD load is under 1. ;-) I've put OpenBSD on LDOM on T1000 SPARC machine to make firewall and spam filtering for Solaris LDOMs. It seems to be very good decision.
I.
By David Chisnall (82.7.192.45) on
Comments
By Mouring (136.162.45.33) mouring@eviladmin.org on http://eviladmin.org
Google uses SPF to advertise their outgoing mail servers. Can't spamd check if the resend is from a machine authorised by the domain owner and treat it as a valid resend if both the original and the reply are from SPF-approved domains? You'd probably want to ignore ?all records when doing this, but anyone who publishes accurate SPF records could then resend from any of their mail servers.
[[//quote]]
Before being forced to move to postini a few years back due to an email address being bounce-bombed (even at that postini helped half my load, but I still had to apply heavy handed procmail filters). I had a simple script that polled SPF entries for a list of "problem children with SPF records" and built a whitelist file for them every night. It worked well.
A simple extension to support this more natively would be interesting. I'm not sure I would accept every SPF record presnted to me, but allowing it to be used as a white/black list entry may be useful.
Comments
By Victor (69.154.100.161) on
> A simple extension to support this more natively would be interesting.
Agreed. I use the SPF records to whitelist Google and others. Found a few scripts on the net to gather and create whitelist. This works well. I then went paranoid with DJB's tcpserver and this helped but I have to deal with the people that have misconfigured servers.
By Anonymous Coward (97.88.184.178) on
What if the SPF record allows 1.0.0.0/8 and 2.0.0.0/8, etc.,? It would take nothing for a spam domain to designate all of Afrinic, for example, as valid senders.
There was a spamd patch floating around [misc@ or tech@ ?] that would allow resends from the same /24 subnet, which is reasonable.
I was called at home during supper one night a few years ago, because some mail wasn't coming through. The sender's first connection came from .10, then .11, and .12 and so forth. The bad part was that the sender was the company buying us, and the emails were the final signing documents. Made me look very bad, indeed, holding up the sale of the company, even if the fix was just whitelisting their /24.
Would be nice if spamd had a knob ("Knobs be damned!") that allowed you to designate the subnet mask (default /32) to apply to the sender.
By Anonymous Coward (dspiteri) on
By Cybil Courraud (82.66.245.132) d@cyb.fr on
1. I was missing bsdly in my conf, thanks for it. Nevertheless, (maybe 'cause I use FBSD, sorry) I couldn't fetch the list. So I replaced :file=http://www.bsdly.net/~peter/bsdly.net.traplist: without 'http://' and it's OK.
2. For SPF, I made a script which fetches "my friends'" mail forwarder IPs and feed my whitelist by domainname. In this list, I met f5.com, fr.ibm.com, bizanga.com, bnpparibas.com, sfr.fr, apple.com etcetera. This kind of use of SPF is only for not delaying (at least for work). Take care of reverse lookup (pf doesn't like unresolved hosts): do reverse lookup hosts with a cronded script before.
3. CIDR is very efficient (even if unfair as we do it for China or Korea). BTW, I add to spamd.conf(5) some lists from my favorites top spam countries (which I'm not communicating with). Here is my script to get a good country ranking (install GeoIP package before):
#! /usr/bin/perl my %db; for ( `spamdb` ) { next if /^SPAMTRAP/; if ( /^(\w+)\|([^\|]+)/ ) { my $kind = $1; my $ip = $2; my $country = `geoiplookup $ip`; $country =~ s/.*, ([\w\s]+)\n/$1/; if ( $country =~ /IP Address not found/ ) { $db{"$kind not found"} .= "$ip "; next; } $db{"$kind $country"}++; } } for ( sort keys %db ) { print $_.": ".$db{$_}."\n"; }4. Honey pot: publish your spammed logins on a poor web page (my catchall gave me some ;). And ... tarpit for pleasure !
Comments
By Andreas Vögele (85.216.54.124) on
We get much more spam from Brazil and the US than from China and Korea.
> BTW, I add to spamd.conf(5) some lists from my favorites top spam countries (which I'm not communicating with). Here is my script to get a good country ranking (install GeoIP package before): [...]
BTW, it's easy to add GeoIP lookups to the Exim mailer. I put the following code into /etc/exim/exim.pl.
use Geo::IP; my $geoip = Geo::IP->new(GEOIP_STANDARD); sub geoip_lookup_address { my $ip_address = shift; my $country_code = $geoip->country_code3_by_addr($ip_address); return $country_code; }This module is loaded with... ...and, for example, later used like this# Look up the country the sender host is located in. warn condition = ... add_header = X-Sender-Host-Country: ${perl{geoip_lookup_address}{$sender_host_address}}By guly (88.149.155.77) on
By Anonymous Coward (84.251.129.228) on
Comments
By Anonymous Coward (97.88.184.178) on
[Not sure why my original reply was deleted.....]
Being able to identify and block ALL hosts would increase the ability to block spam. But what kind of an answer is that?
Would you really block incoming bid requests from Exchange or MDaemon or other Windows mail servers? I doubt the sales department would let you get away with it. Under what scenario would you possibly want to block Windows hosts [other than a trivial vanity domain for technical xenophobes] ?
Comments
By Morten Larsen (morten1980) on http://blog.unx.dk/
Blocking or greylisting "Windows XP" has worked well for me.
By Anonymous Coward (85.158.44.149) on
>
> [Not sure why my original reply was deleted.....]
>
> Being able to identify and block ALL hosts would increase the ability to block spam. But what kind of an answer is that?
>
> Would you really block incoming bid requests from Exchange or MDaemon or other Windows mail servers? I doubt the sales department would let you get away with it. Under what scenario would you possibly want to block Windows hosts [other than a trivial vanity domain for technical xenophobes] ?
Blocking, agreed. But it's useful for greylisting; if you only want to do partial greylisting, Windows hosts are a good target for being greylisted.
By Anonymous Coward (12.158.188.186) on
Comments
By Sean Cody (sean) on I don't work here.
Fixed. Converting to HTML by hand when I should be sleeping is a lesson I keep having to relearn. Regardless thanks.
By Chris Bennett (chrisbennett) webmaster@bennettconstruction.us on www.bennettconstruction.us
I had done some manual changes to nixspam, so I thought I'd try manually downloading traplist.
wget -m -nd - failed
lynx -source - failed
Weird part - both work just fine a home!!
wget, lynx, firefox at home work fine.
Not a clue why fails on server. pf.conf problem? My server is blacklisted somehow?
Comments
By Peter N. M. Hansteen (pitrh) peter@bsdly.net on http://bsdly.blogspot.com/
sounds distinctly odd. With IP address (or hostname) and times in hand I could check my logs to see what turns up (the email address works).